ScyllaDB Cloud Network Connectivity: Transit Gateway Connection
ScyllaDB Cloud is a managed NoSQL Database-as-a-Service based on the leading open-source database engine ScyllaDB. It is designed for extreme performance, low latency, and high availability. It is compatible with the Cassandra Query Language (CQL) and Amazon DynamoDB APIs, making it a possible replacement for many solution architects pursuing performance.
This article is about ScyllaDB Cloud network connectivity management. It will show how to use ScyllaDB Cloud to connect to the customer’s application using a transit gateway.
ScyllaDB Cloud Network Connectivity
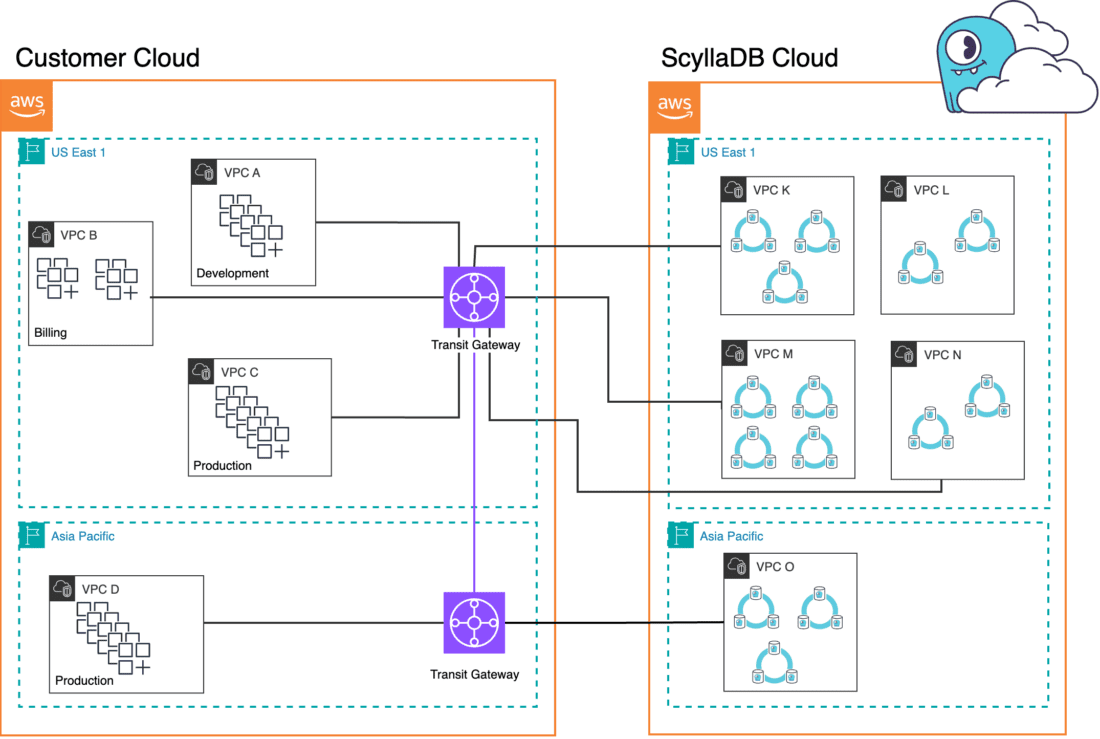
In response to customer demand, ScyllaDB Cloud now offers two solutions for managing connectivity between ScyllaDB Cloud and customer application environments running in Amazon Web Services (AWS) or even in hybrid cloud setups. In addition to VPC peering, we now support Transit Gateway Connection.
Two Connectivity Options
VPC peering connection has been supported for years. It is an excellent solution for connectivity in non-complex network setups. However, managing many VPC peering connections can be cumbersome, error-prone, and challenging to audit.
This problem became more severe at scale, and another tool from the arsenal of AWS became necessary.
The Transit Gateway Connectivity feature was added to ScyllaDB Cloud in February 2024. It enables our customers to use Transit Gateways as part of their configuration. It adds another way to connect to ScyllaDB Clusters. The feature is available in clusters deployed in ScyllaDB Cloud as well as clusters deployed on the customer’s own AWS accounts, via the bring-your-own-account feature (BYOA).
Transit Gateway Connection allows connection using a centralized hub that simplifies the connectivity and routing. This helps organizations connect multiple VPCs, Load Balancers, and VPNs within a single, scalable gateway. It acts as a transit hub for routing traffic between various network endpoints, providing a unified solution for managing connectivity across complex or distributed environments.
The Transit Gateway simplifies the management of intricate networks created by introducing a more centralized hub-and-spokes model.
That simplifies configuring and monitoring the network connectivity, streamlines operations, and improves visibility.
Moreover, it acts as a central place to apply security policies and access controls – thereby strengthening network security and improving auditability.
Configure Transit Gateway Connection in ScyllaDB Cloud
Configuring the Transit Gateway in ScyllaDB Cloud is straightforward.
Prerequisites
- ScyllaDB Cloud account. If you don’t have an account, you can use a free account. Get one here: ScyllaDB Cloud.
- Basic understanding of AWS networking concepts (VPCs, CIDR subnets, Resource Shares, route tables).
- AWS Account with sufficient permissions to create network configurations.
- 30 minutes of your time.
Step 1: ScyllaDB Cloud Cluster
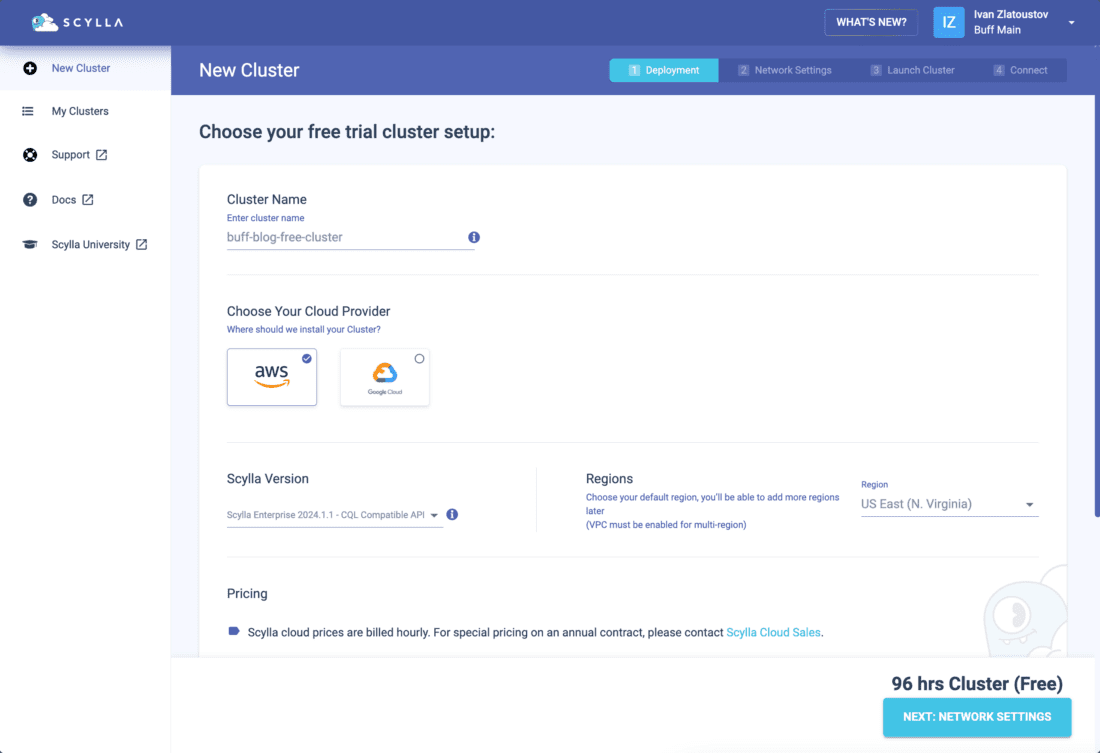
Login to ScyllaDB Cloud and create a New Cluster. Depending on your account, you can either use the Free trial or Dedicated VM option. For this, I am using a free trial; if you choose a Dedicated VM, your screen might be slightly different.
Please select AWS as your Cloud Provider and click Next.
As of the time of this blog, we support only AWS Transit Gateway connection. Support for Network Connectivity Center(NCC) or similar technologies for Google Cloud Platform(GCP) or other clouds will be added in time.
On the next screen, Cluster Properties under Network Type, you should select VPC Peering / Transit Gateway to enable network connectivity, and then you can confirm with the Create Cluster button below.
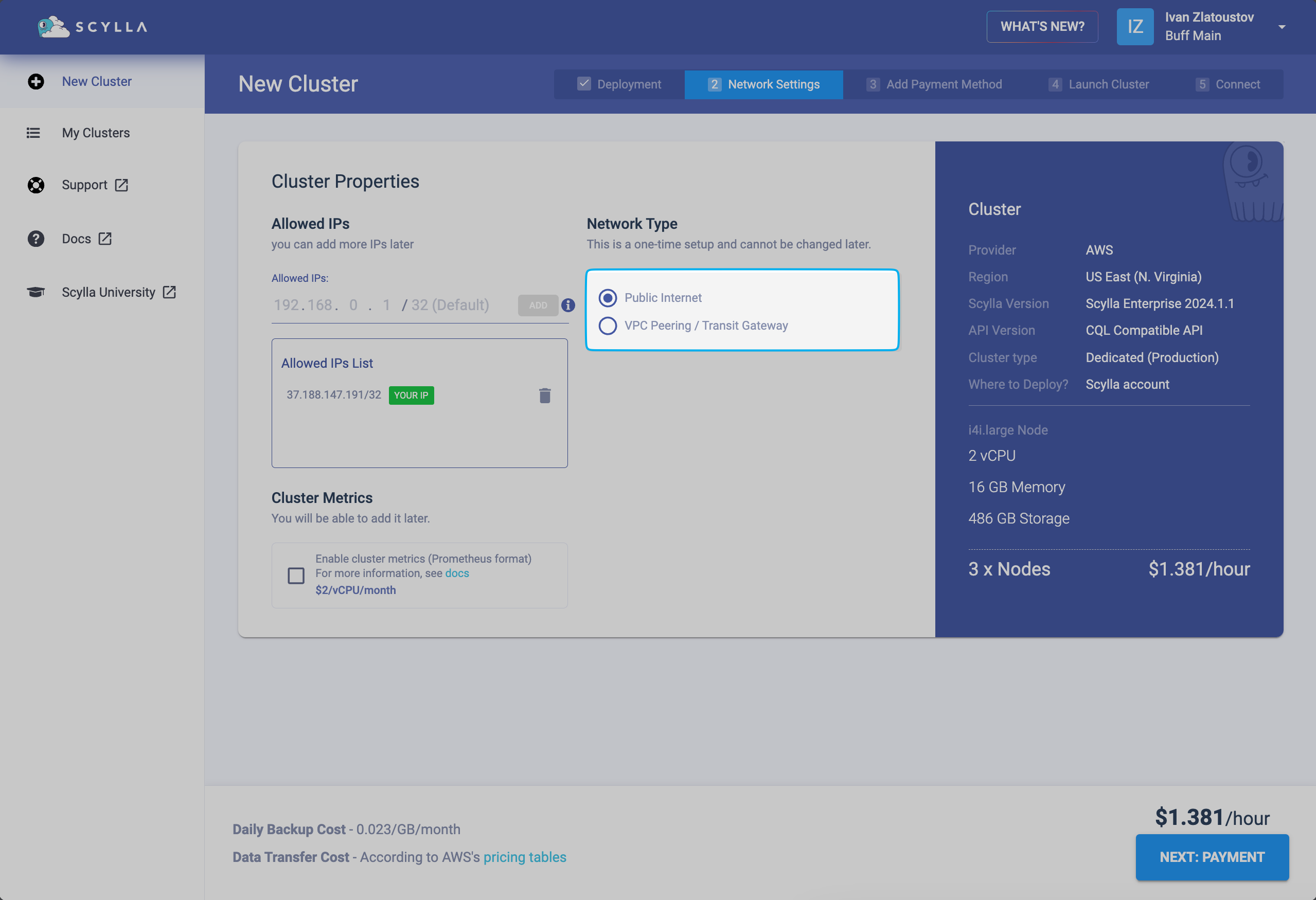
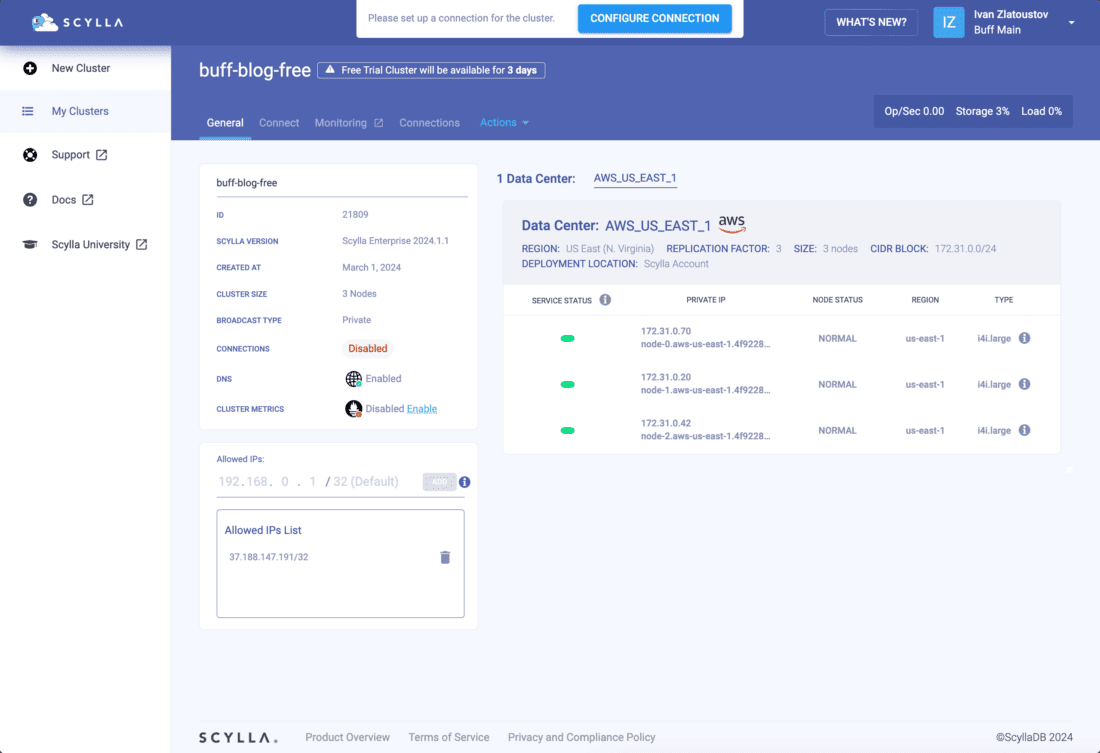
The ScyllaDB cluster will be created shortly. Once it’s created, select the cluster.
Step 2: Provision AWS Transit Gateway
The following steps for provisioning of the transit gateway have to be done in your AWS account. Alto transit gateway can connect to transit gateways in other regions (inter-region); it can only connect VPCs from the same region.
The transit gateway should be deployed in the same region as the ScyllaDB cluster. In this case, this is us-east-1.
If you are not familiar with creating a transit gateway, the following guide can help:
Configure AWS Transit Gateway (TGW) VPC Attachment Connection.
It is a good idea to set Auto accept shared attachments. It will make your TGW automatically accept attachment requests from other accounts, including ScyllaDB Cloud.
For the next step, we will need the Transit Gateway ID and RAM Resource Share APN.
Step 3: Configuring Transit Gateway Connection in ScyllaDB Cloud
The next step is to configure the network connection.
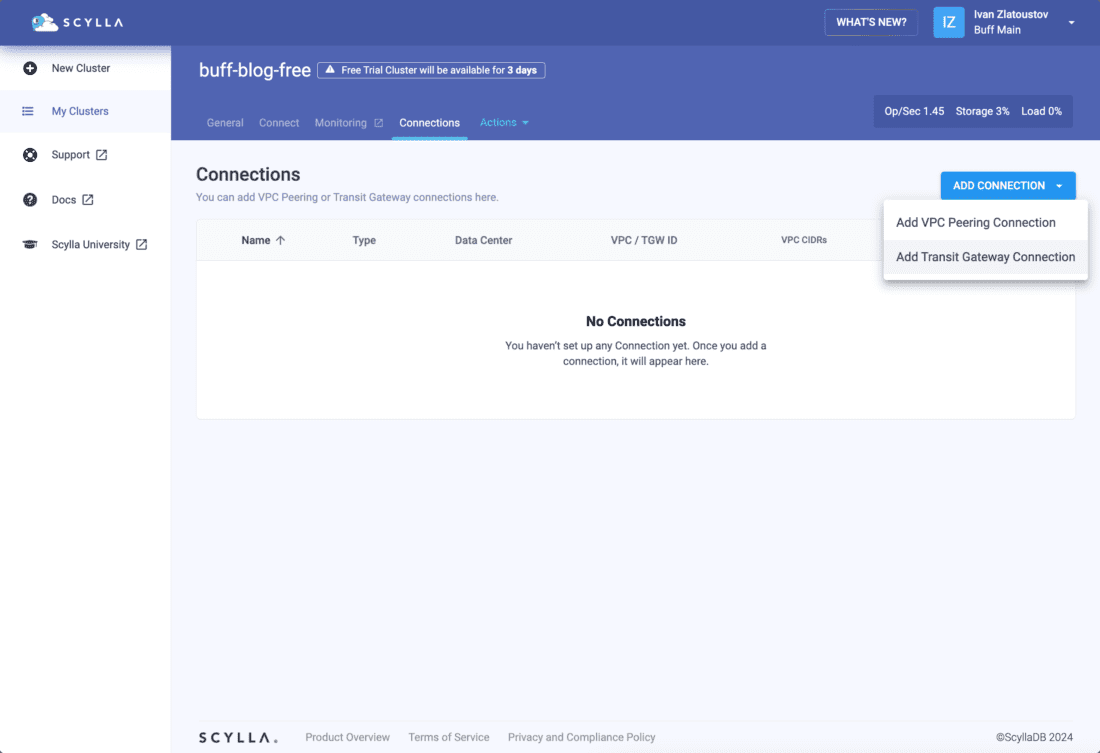
Select the Connections tab. You will be navigated to the Connections screen below.
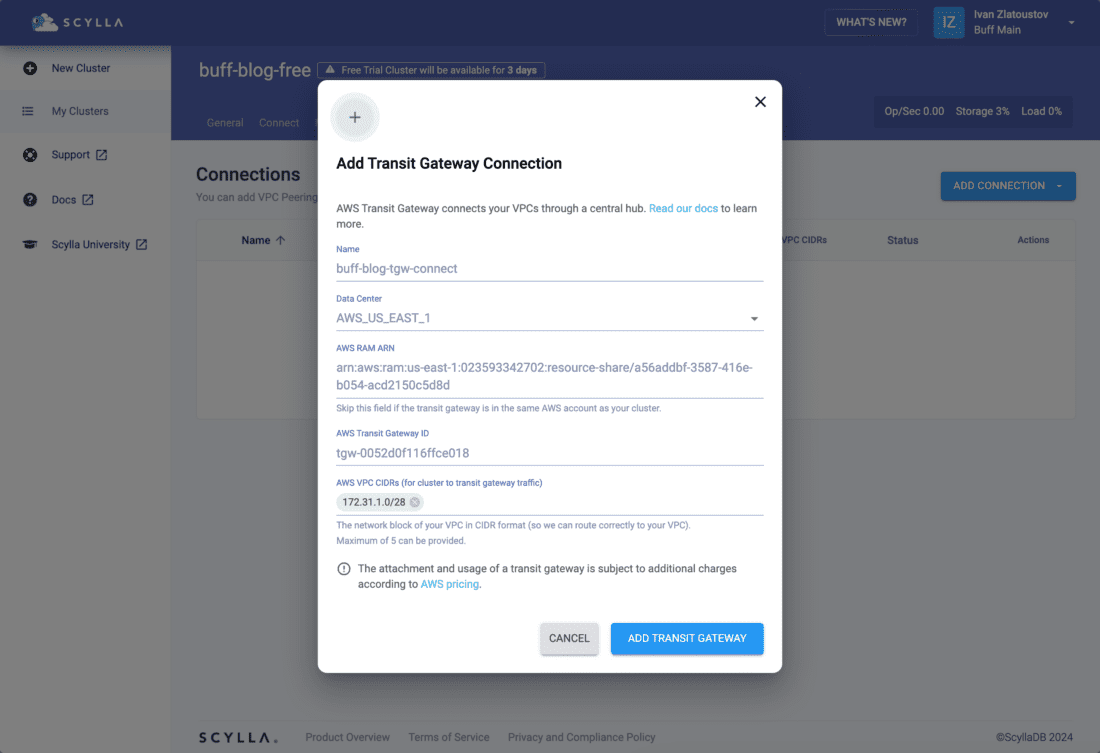
Select Add Transit Gateway Connection and when prompted, provide a custom Name. This is how the connection will be visualized in ScyllaDB Cloud.
The Data Center should be the region where the TGW is located.
Get the AWS RAM ARN from your AWS Resource Share as configured in the AWS setup in the previous step and the Transit Gateway ID transit gateway from AWS Transit Gateways (12-digit ID).
Provide the chosen VPC CIDR to route the traffic and proceed with Add Transit Gateway.
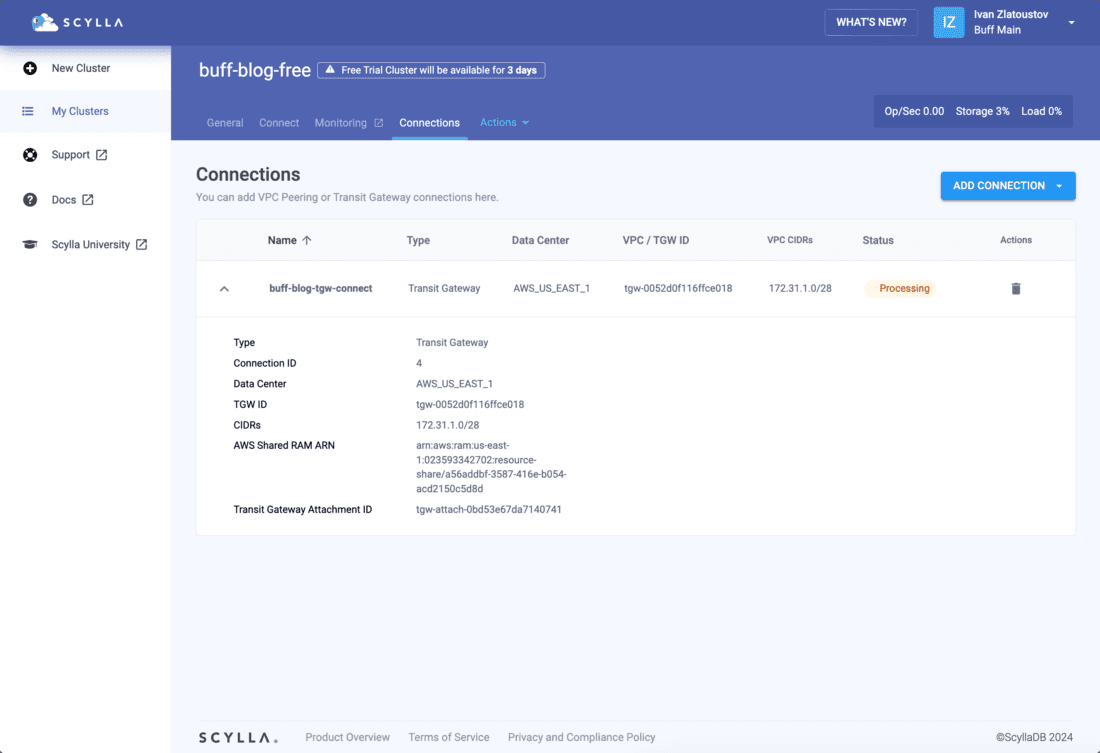
The processing will take some time.
If you followed my advice above, the connection will be accepted automatically. Otherwise, you will have to go to your AWS account to accept the connection.
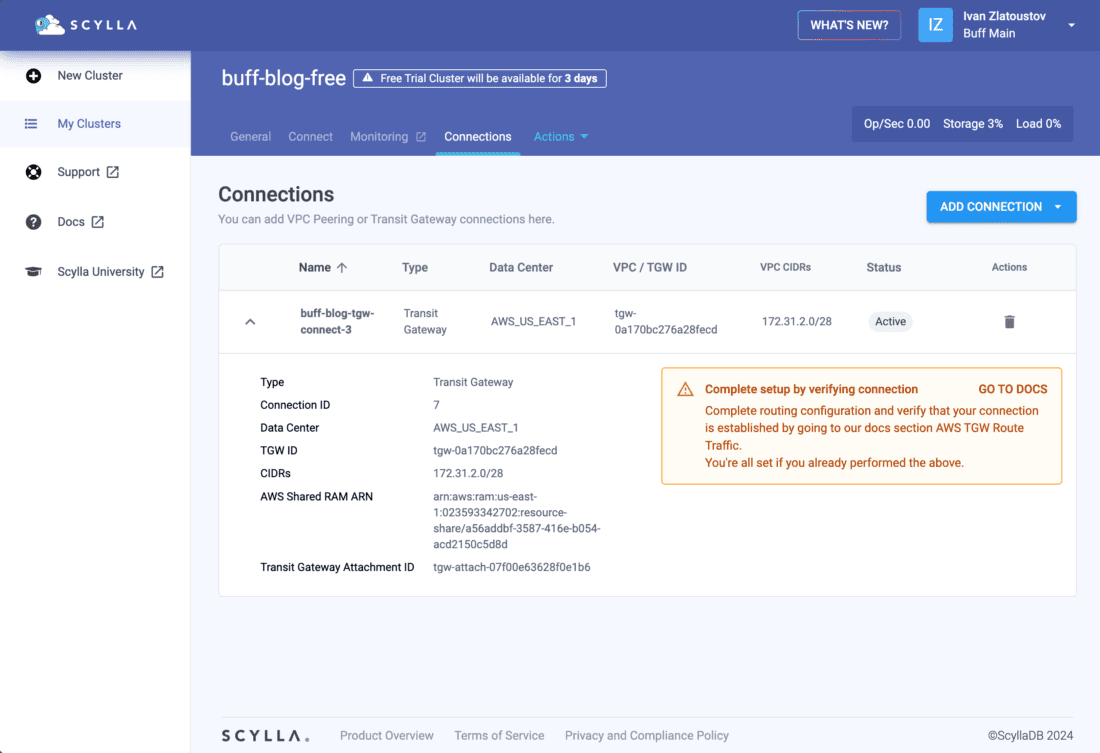
Once the connection is active, the attached networks from the customer AWS account and the ScyllaDB Cloud should see each other over the networks as defined.
You can go to the ScyllaDB Documentation if you need help verifying the connection.
Cost & Billing
Amazon will charge the network components to the AWS account associated with each respective network component. This might be confusing at first. It means that bills will be sent to different accounts when connecting components from different accounts.
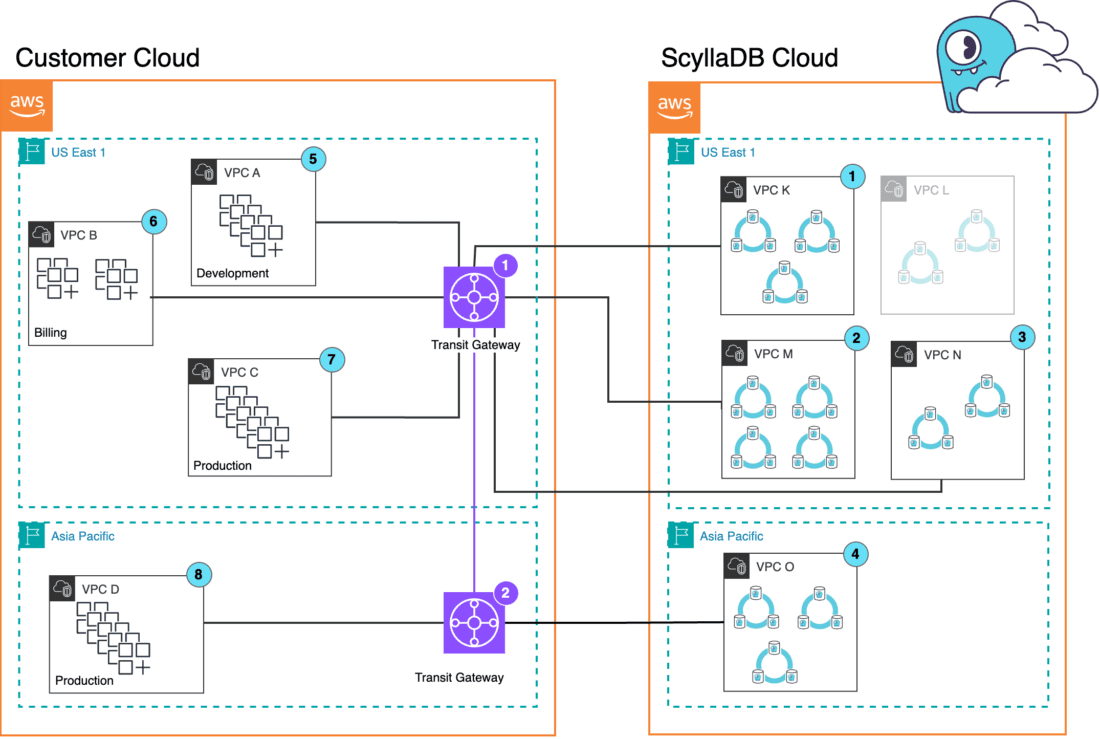
In our cost example below, the database clusters are in ScyllaDB Cloud, but the applications are in the customer AWS account. For illustration purposes, we have databases and applications in different regions, with multiple transit gateways and peering. It is a complicated setup designed to show the different categories of charges.
The expenses that occur using Transit Gateway Connection are listed and explained below.
AWS Transit Gateway attachment hourly charges
AWS charges for each network component attached to the transit gateway. The typical cost per hour is $0.05 per attachment (us-east-1). The price varies by region for ap-northeast-2 it is $0.07
Attachments are considered all VPCs from the diagram above (1,2,3,4,5,6,7,8) and both transit gateways, TGW1 and TGW2. Attachments are also considered other network components like VPN connections, VPC peering, gateways etc. which are excluded from this setup.
In our example, we have the following components:
Components connected to TGW1 (price for attachment $0.05 us-east-1):
VPC 1,2,3,4 will be billed to ScyllaDB Cloud
4 x $0.05 = $0.20 per hour
VPC 5,6,7 and TGW2 will be billed to Customer AWS Account
5 x $0.05 = $0.25 per hour
Components connected to TGW2 (price for attachment $0.07 ap-northeast-2)
VPC 8 and TGW1 will be billed to Customer AWS Account
2 x $0.07 = $0.14 per hour
Monthly the charges will be as follows:
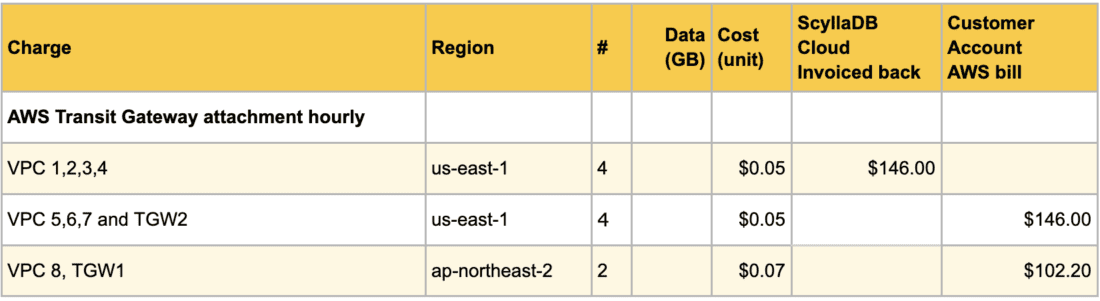
Transit Gateway data processing charges
Transit Gateway Data Processing costs $0.02 per 1 GB in most regions.
Data processing is charged to the AWS account that owns the VPC. Assuming 2 TB of symmetrical traffic for simplicity.
VPC 1,2,3,4 will be billed to ScyllaDB Cloud 4 x 2048 GB x $0.02 = $163.84
VPC 5,6,7,8 will be billed to Customer AWS Account 4 x 2048 GB x $0.02 = $163.84
Monthly the charges will be as follows:
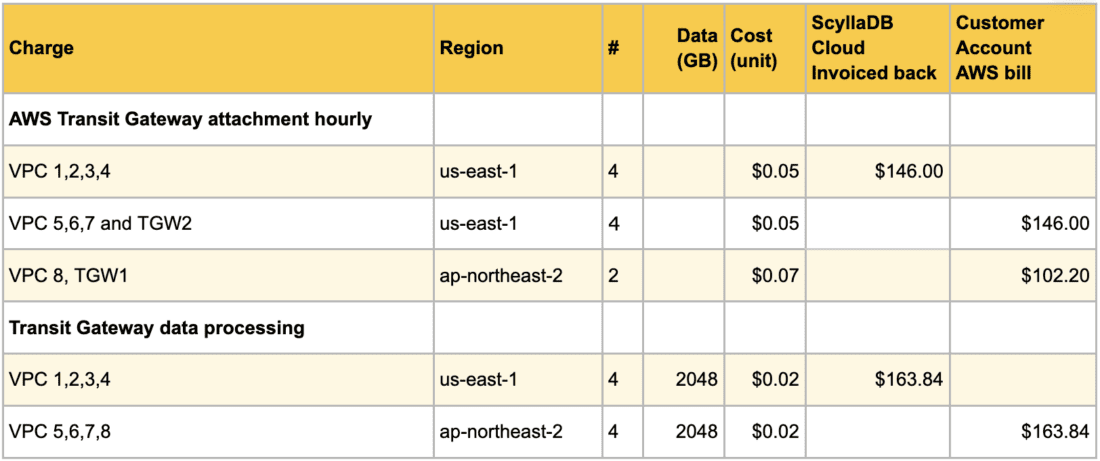
Transit Gateway data processing charge across peering attachments
These are the peering fees between two or more Transit Gateways. Only outbound traffic will be charged as standard traffic between regions.
Charges differ by region, but the typical cost is $0.02.
The monthly charges will be as follows:
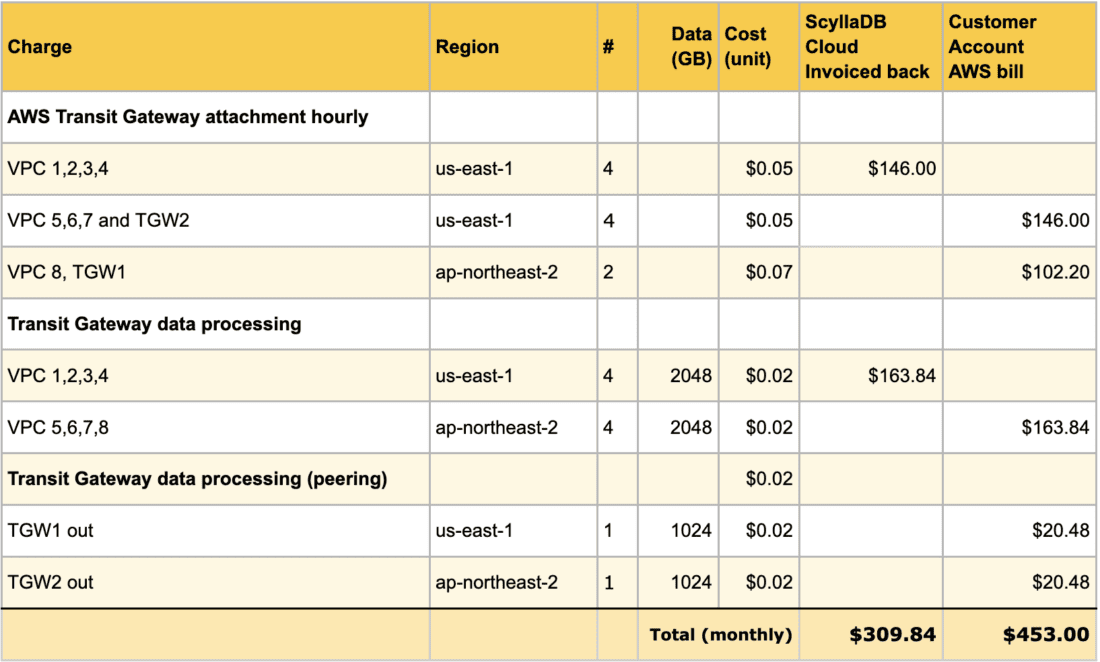
All charges in the ScyllaDB Cloud Column total of $324.44 will be included in ScyllaDB Cloud’s monthly billing report and passed back to the customer.
All charges in Customer Account will appear in the customer AWS bill.
Bring your own account (BYOA)
Customers can use ScyllaDB Cloud to deploy databases in their AWS account.
In this case, all charges will be applied to the customer’s account or accounts. Since there will be no charges in ScyllaDB Cloud, nothing will be passed with the monthly bill.
Combining Transit Gateways, VPC peering, VPN connections in the same network setup is possible. ScyllaDB Cloud supports this configuration to provide flexibility and cost optimization.
ScyllaDB Cloud Network Connectivity Overview
ScyllaDB Cloud offers two network connectivity features. Both VPC Peering Connection and Transit Gateway Connection enable seamless and efficient connectivity between customer applications and highly performant ScyllaDB database clusters.
We invite you to explore ScyllaDB Cloud and experiment with the network connections to match your unique application requirements and budget
- You can experiment with this feature in ScyllaDB Cloud.
- We welcome your questions in our community forum and Slack channel.
- Alternatively, you can use our contact form.